NiFi Security Essentials: Closing Gaps in Real-Time Data Movement
![]()
Today, enterprises rely heavily on real-time data movement to fuel analytics, operational decision-making, and customer experiences. Whether it’s a retail platform syncing inventory across channels or a logistics company tracking shipment status in real time, data in motion has become critical to business success.
But with speed comes vulnerability. Real-time data flows are uniquely exposed to security risks, from interception to unauthorized access. Fortunately, Apache NiFi, a powerful platform for automating the flow of data across disparate systems, provides robust features to build secure data pipelines.
In this blog, we’ll explore the security risks of real-time data movement, how NiFi’s built-in security features help address them. Further, we will walk you through actionable best practices to ensure your data in motion stays protected.
Understanding Security Risks in Real-Time Data Movement
Real-time data pipelines involve continuously transferring data from multiple sources (e.g., IoT devices, databases, APIs) to destinations like data lakes, analytics platforms, or dashboards, often in milliseconds.
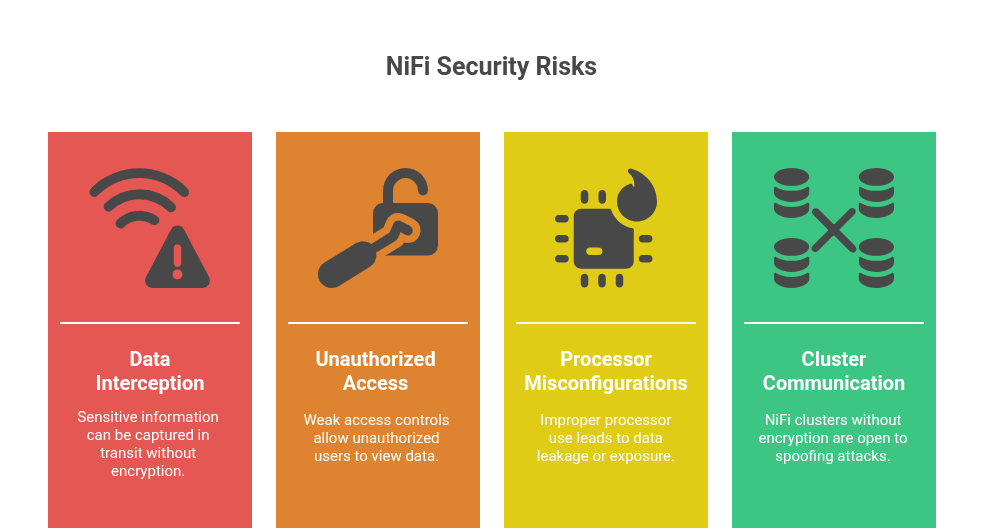
But this speed and complexity introduce a set of unique security challenges:
Common Vulnerabilities:
- Data Interception: Without encryption, sensitive information can be captured in transit.
- Unauthorized Access: Weak access controls can allow bad actors or unqualified users to manipulate or view data flows.
- Processor Misconfigurations: Improper use of NiFi processors can lead to data leakage or unintended exposure.
- Cluster Communication Risks: NiFi clusters without proper SSL/TLS encryption are open to spoofing or man-in-the-middle attacks.
These issues aren’t just theoretical. Data pipeline vulnerabilities can lead to breaches, regulatory penalties, and loss of customer trust.
Apache NiFi Security Model: What’s Built-In
Apache NiFi was designed with security as a foundational principle, not an afterthought. Its architecture supports a comprehensive set of security controls that make it well-suited for enterprise-grade, secure data ingestion and flow orchestration.
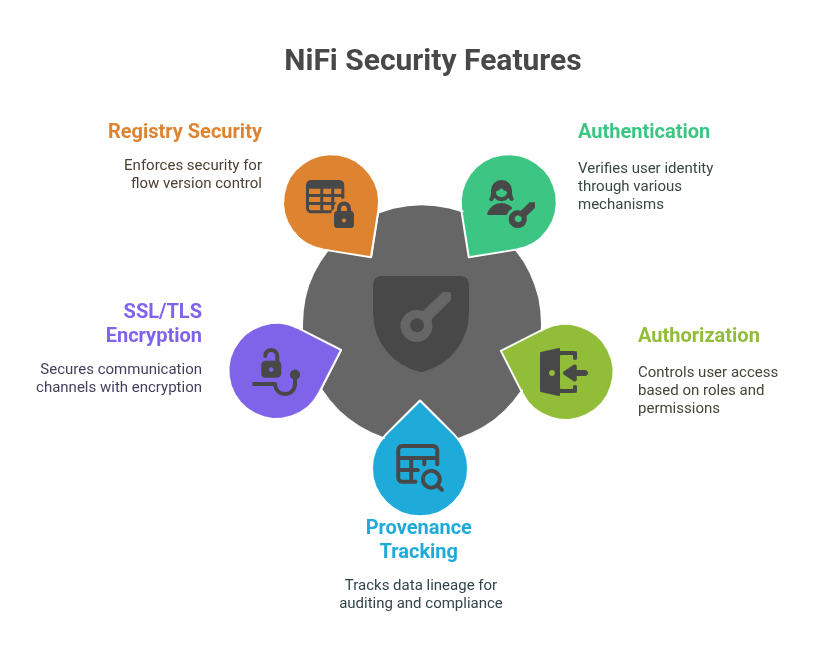
Here’s a breakdown of the key security features NiFi offers out of the box:
1. Authentication & Authorization
NiFi supports multiple authentication mechanisms, including LDAP, Kerberos, and OpenID Connect (OIDC), enabling seamless integration with enterprise identity providers.
Once authenticated, users are governed by Role-Based Access Control (RBAC) that allows administrators to define highly granular permissions, down to individual process groups, processors, and UI components. This ensures that only the right users have access to the right capabilities within the flow environment.
2. Provenance Tracking
Data lineage is a first-class feature in NiFi. Every flowfile is tracked from the moment it enters the system until it leaves, with full visibility into what transformations occurred, who performed them, and when.
This end-to-end provenance tracking is critical not only for auditing and compliance (e.g., HIPAA, GDPR) but also for troubleshooting and incident response.
3. SSL/TLS for Secure Communication
NiFi supports SSL/TLS encryption across all major communication channels:
- Web UI access (HTTPS)
- Site-to-Site (S2S) protocol between remote NiFi instances
- Inter-node communication within clustered deployments
Properly configured, these channels ensure that data in motion is encrypted and protected against eavesdropping and tampering.
4. NiFi Registry Security
When using NiFi Registry to version control your flows, you can enforce authentication and authorization for key operations like committing new versions, importing flows, and rolling back changes.
Registry instances can be secured via mutual TLS, and when backed by Git, benefit from signed commits and auditability. This enforces change control policies while maintaining transparency into pipeline evolution.
Best Practices to Secure Data Pipelines in Apache NiFi
Apache NiFi provides robust security features out of the box, but simply enabling them isn’t enough. To truly secure your real-time data pipelines, you need to apply a consistent set of hardening practices, from authentication and encryption to operational visibility and flow governance.
Below are industry-proven best practices to help you maximize the security posture of your NiFi environment, both at the node and cluster levels.
Read More– How DFM Streamlines End-to-End Cluster Management in Apache NiFi
1. Authentication & Authorization
Secure NiFi deployments start with strong identity management. Apache NiFi supports LDAP, Kerberos, and OpenID Connect (OIDC) for user authentication and provides Role-Based Access Control (RBAC) to manage user permissions across the system.
To simplify this further, Data Flow Manager offers seamless integration with enterprise identity providers such as LDAP, Kerberos, and SSO. It streamlines the configuration process, eliminating the need for complex manual setup and reducing the likelihood of misconfigurations.
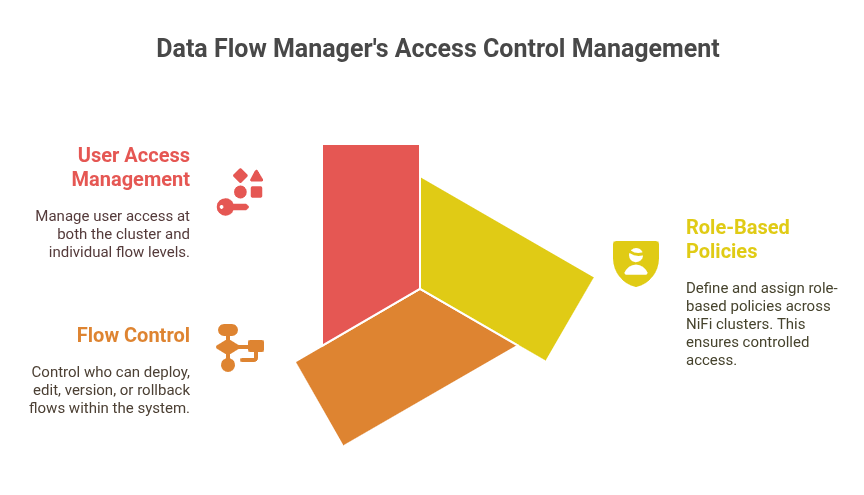
Beyond authentication, Data Flow Manager also enhances access control by allowing administrators to:
- Define and assign role-based policies across one or more NiFi clusters.
- Control who can deploy, edit, version, or rollback flows.
- Manage user access at both the cluster and flow levels.
By centralizing and simplifying user management, Data Flow Manager ensures that only the right people have access to the right resources, supporting both security and operational efficiency at scale.
2. Secure Communication
Always enable HTTPS and TLS across:
- Web UI access
- Site-to-Site (S2S) communication between NiFi instances
- Inter-node communication in clustered deployments
Use certificates signed by a trusted Certificate Authority (CA), and enforce mutual TLS where possible. Regularly rotate certificates, monitor their expiration, and promptly revoke unused or compromised keys.
These practices ensure that data in motion is encrypted, communication channels are authenticated, and eavesdropping or spoofing attempts are neutralized.
3. Data Provenance & Centralized Logging
Enable full provenance tracking to maintain a detailed lineage of every flowfile, when it entered the system, where it traveled, what changed, and who made those changes. This is especially critical in regulated industries or in flows handling PII, financial, or healthcare data.
To enhance visibility and ensure auditability, forward NiFi logs and provenance events to a centralized SIEM such as Splunk, ELK, or Graylog.
Here, Data Flow Manager proves invaluable, offering centralized logging and insights into user actions across clusters, making it easier to monitor access patterns, flag suspicious behavior, and meet compliance standards.
4. Restrict High-Risk Components
Limit the use of powerful processors such as ExecuteScript, ExecuteProcess, or InvokeHTTP, which could execute arbitrary code or transmit data to unintended endpoints.
Leverage NiFi’s Restricted Components feature to allow usage only by trusted admins. In multi-tenant environments, this reduces the attack surface and enforces internal policy compliance.
5. NiFi Registry Hardening
If you’re using NiFi Registry for versioning flows, ensure it’s secured with:
- TLS encryption for Registry communication.
- Access control policies on version access, modification, and rollback.
- Integration with Git-backed repositories for version history and change verification.
Signed commits, combined with Registry security, create a reliable audit trail, essential for regulated workflows and change governance.
Advanced Security Measures for Enterprise Deployments
For organizations operating in regulated industries or those with elevated security and compliance requirements (e.g., HIPAA, GDPR, PCI DSS), foundational hardening isn’t enough. You need to adopt advanced security practices that address deeper risks at scale, particularly in distributed, multi-cluster, and hybrid environments.
Here are enterprise-grade strategies to further fortify your NiFi deployments:
1. Integrate with SIEM Platforms
Connecting NiFi with a Security Information and Event Management (SIEM) system such as Splunk, ELK Stack, or IBM QRadar enables real-time log aggregation, threat detection, and automated alerting. You can stream NiFi’s application logs, provenance data, and user activity into your SIEM to:
- Detect unauthorized access attempts.
- Monitor flow anomalies and configuration changes.
- Satisfy regulatory logging and audit trail requirements.
This integration enhances your incident response capability and aligns NiFi with broader enterprise security monitoring frameworks.
2. Encrypt FlowFile Content at Rest
While NiFi encrypts data in transit, enterprises should also consider encrypting FlowFile content at rest, especially when handling sensitive or regulated data.
You can achieve this by:
- Using PGP/GPG encryption within custom processors.
- Integrating with external secrets managers like HashiCorp Vault for key management.
- Encrypting critical fields inside flowfiles before storing or forwarding them.
This adds a second layer of protection, ensuring that even if a disk, archive, or flowfile repository is compromised, the content remains inaccessible without the encryption keys.
3. Isolate Critical Workloads
Not all data flows are created equal. Workflows involving highly sensitive data, such as patient records, payment transactions, or IP, should be segmented from general-purpose pipelines.
- Deploy dedicated NiFi clusters for sensitive workloads.
- Use separate process groups with restricted user access.
- Apply heightened monitoring and auditing policies to these flows.
Isolation reduces lateral movement risks and helps maintain tighter control over privileged environments, a common requirement in zero-trust architectures.
4. Enforce Network-Level Security Controls
NiFi should never be exposed directly to the public internet without protection. Enforce robust network segmentation and access policies, including:
- VPCs and private subnets for cloud deployments.
- Ingress/egress firewall rules to restrict communication only to known, trusted systems.
- VPN or bastion access for internal users and admins.
Combined, these controls prevent external threats and reduce the blast radius of internal misconfigurations or breaches.
Conclusion
Securing real-time data movement is a necessity for any organization handling sensitive or business-critical information. Apache NiFi offers a solid foundation with its built-in authentication, encryption, and flow governance features. But true security comes from applying best practices consistently across authentication, communication, logging, and access control.
The combination of NiFi’s native capabilities with tools like Data Flow Manager and extending protections through encryption, isolation, and SIEM integration proves to be a game-changer. Enterprises can confidently scale their data infrastructure while staying compliant and secure. Investing in a proactive, layered security approach ensures your data pipelines are not just fast and flexible but also resilient and trustworthy.
![]()

